Given the exponential growth of cloud adoption, securing cloud environments has become a paramount concern for modern enterprises. As organizations increasingly rely on cloud services to streamline operations and enhance agility, the threat landscape has evolved to target these environments with increasing sophistication. Consequently, the need for robust cloud security measures has never been more pressing. One of the most effective strategies for achieving this is the integration of Infrastructure as Code (IaC) with cloud security practices.
IAC is the Gateway to Automation
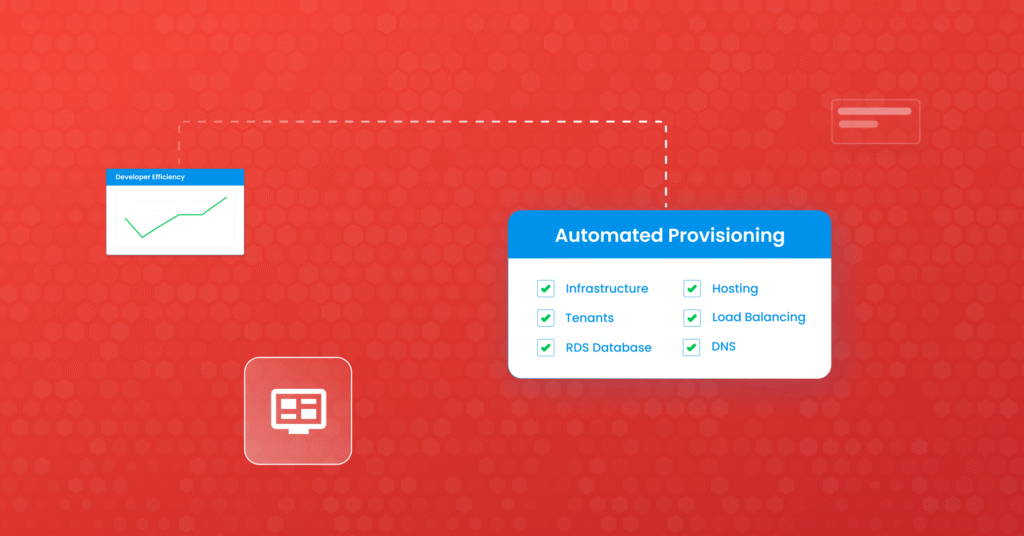
IaC involves using code to manage and provision infrastructure resources, allowing for a more automated and reproducible approach to cloud deployments. This method enhances efficiency and provides a higher level of security, as it ensures consistency in configuring and monitoring cloud infrastructure components. By incorporating IaC into the cloud security framework, organizations can achieve a more cohesive and comprehensive approach to safeguarding their data and applications in the cloud.
The benefits of IaC in cloud security are manifold. It enables organizations to automate the provisioning and deployment of security controls, ensuring that security policies are consistent across all environments. Additionally, IaC allows for creating immutable infrastructure, where changes are made through code deployments rather than manual updates, thereby reducing the risk of human error. Furthermore, IaC facilitates the creation of detailed audit trails essential for compliance and forensic investigations.
Integrating IaC with cloud security practices is a critical step in ensuring the security and integrity of cloud environments. By leveraging the power of IaC, organizations can automate and streamline their security processes, reducing the vulnerability of their cloud infrastructure to cyber threats and maintaining a high level of security and compliance.
Learn how IaC can revolutionize your cloud security strategies and safeguard your digital assets in the ever-evolving threat landscape.
The Growing Criticality of Cloud Security
The need for robust cloud security measures has become increasingly critical. One of the most effective ways to ensure the security of cloud environments is by adopting an infrastructure such as Code (IaC). This approach streamlines the process of deploying and managing infrastructure and provides unparalleled security benefits. In this article, we delve into the importance of IaC in securing cloud environments and explore how you can leverage that to enhance overall security and compliance.
The rise of cloud computing has brought numerous benefits, including scalability, flexibility, and cost-effectiveness. However, it has also introduced new security challenges. Traditional security measures, such as firewalls and antivirus software, are no longer sufficient to protect cloud environments. Cloud infrastructure's complexity and dynamic nature require a more sophisticated approach to keep pace with the rapid changes and frequent deployments typical in the cloud.
The Role of IaC in Cloud Security
Infrastructure as Code (IaC) is a way to manage and provision computing infrastructure through scripts rather than manual processes. This approach allows for the automation of infrastructure setup, configuration, and deployment. By using IaC, organizations can ensure that their cloud infrastructure configuration is consistent and meets the required security standards. This not only reduces the risk of human error but also enables faster and more efficient resource deployment.
Benefits of IaC in Cloud Security
The adoption of IaC in cloud security provides several significant benefits:
- Consistency: IaC ensures that infrastructure is deployed consistently across different environments, reducing the risk of misconfigurations and non-compliance issues.
- Automation: IaC automates the deployment and management of infrastructure, reducing the need for manual intervention and the associated risks.
- Version Control: IaC allows for version control systems, enabling teams to track changes and collaborate more effectively.
- Improved Compliance: IaC helps organizations maintain compliance with regulatory requirements by ensuring that infrastructure is configured correctly and consistently.
Implementing IaC for Cloud Security
Implementing IaC for cloud security involves several key steps:
- Choose an IaC Tool: Select a suitable IaC tool such as Terraform, Ansible, or Puppet. Each tool offers specific features and benefits.
- Define Infrastructure Requirements: Determine the specific infrastructure requirements, including network configurations, user access, and security settings.
- Write IaC Scripts: Create scripts that define the infrastructure requirements and ensure they are correctly configured.
- Test and Validate: Test the IaC scripts to ensure they are error-free and correctly deploy the infrastructure.
- Deploy and Monitor: Deploy the IaC scripts and monitor the infrastructure to ensure it functions as intended.
IaC Security Best Practices
To maximize the security benefits of IaC, organizations should adhere to several best practices:
- Use Secure Storage: securely Store IaC scripts and sensitive data to prevent unauthorized access.
- Implement Role-Based Access Control: Define and enforce role-based access control to ensure only authorized personnel can manage the infrastructure.
- Regularly Update Scripts: Keep IaC scripts up-to-date to reflect changes in infrastructure requirements and patch any vulnerabilities.
- Monitor and Log: Monitor and log all infrastructure activities to detect and respond to security threats.
Several organizations have successfully implemented IaC to enhance their cloud security. For instance, a leading financial institution used IaC to automate the deployment of its cloud infrastructure, reducing the risk of misconfigurations and improving compliance with regulatory requirements.
Future of IaC in Cloud Security
As cloud computing continues to evolve, using IaC in cloud security is expected to become even more prevalent. New tools and technologies are emerging to enhance further the security benefits of IaC, including advanced encryption and secure storage solutions.
Securing cloud environments is a critical concern for organizations of all sizes. Organizations can significantly enhance their cloud security by adopting Infrastructure as Code (IaC), ensuring consistent configuration, automation, and compliance. As the digital landscape continues to evolve, the importance of IaC in cloud security will only grow, making it an essential part of any cloud strategy.
You may also be interested in 4 Examples of the Power of Infrastructure as Code - DuploCloud
Eliminate DevOps hiring needs. Deploy secure, compliant infrastructure in days, not months. Accelerate your launch and growth by avoiding tedious infrastructure tasks. Join thousands of Dev teams getting their time back. Leverage DuploCloud DevOps Automation Platform, backed by infrastructure experts, to automate and manage DevOps tasks. Drive savings and faster time-to-market with a 30-minute live demo
.